Elliptic Curve Cryptography Support for Certificates
The DNSimple team is pleased to announce support for Elliptic Curve Cryptography (ECC) for SSL certificates!
Previously, we only supported SSL certificates signed with RSA keys. With these new changes, you can take your security one step further. In this post, we'll talk about why this feature is so cool and how to get ECC SSL certificates.
Why is ECC important?
Signing algorithms rely on complex equations to create private and public keys through time-consuming, resource-heavy processes. As technology evolves, and new cryptography solutions are created, we have to keep up with maintaining secure systems that are as threat-free as possible. That's where ECC comes in.
The main advantage of using ECC instead of RSA, the current gold standard, is that it provides the same level of security but uses shorter keys. This means faster processing in some operations, lower bandwidth, and lower energy consumption. So it's not just faster — it's also more environmentally friendly.
The U.S. National Institute of Standards and Technology (NIST) has also started recommending the ECDSA Algorithm for digital signatures in its Suite B set of recommended algorithms.
How does it work?
When we roll out an impactful feature like this, we do it gradually using Feature Flags to deal with any edge cases as they pop up. In this case, we're progressively increasing the percentage of ECC commercial certificates that we issue until no more RSA certificates are issued. If you want to ensure which signing algorithm will be used for your certificates, you can use a custom Certificate Signing Request.
Custom CSRs using an EC key
If you're eager to try this new feature, we can help you expedite an SSL certificate using ECC. Provide us with a custom Certificate Signing Request (CSR), and we'll validate it and issue a new SSL certificate using the key you provided in the CSR.
Let's look at how this works.
First we need to generate an ECC private key:
$ openssl ecparam -name secp384r1 -genkey -noout -out ecdsa-secp384r1.pem
We support two ECC curves:
- X9.62/SECG curve over a 256 bit prime field (prime256v1)
- NIST/SECG curve over a 384 bit prime field (secp384r1)
The choice depends on your needs. This is how these ECC curves relate to RSA according to NIST SP 800-57 Part 1 Rev. 5:
| RSA key length | ECC key length | Conclusion |
|---|---|---|
| 2048 | 224 - 255 | You can use prime256v1 |
| 3072 | 256 - 383 | You can use secp384r1 |
| 7680 | 384 - 511 | You can use secp384r1 |
Once we have the private key, we can generate a CSR for the domain using the following openssl command (make sure you replace the -subj with your data or remove the parameter to follow the interactive wizard):
$ openssl req -new -key ecdsa-secp384r1.pem -nodes -out csr-ecdsa-secp384r1.pem -subj "/C=US/ST=FL/L=Melbourne/O=dnsimple/CN=ecdsakey00.jacegu.work"
The next step is to purchase your commercial certificate:
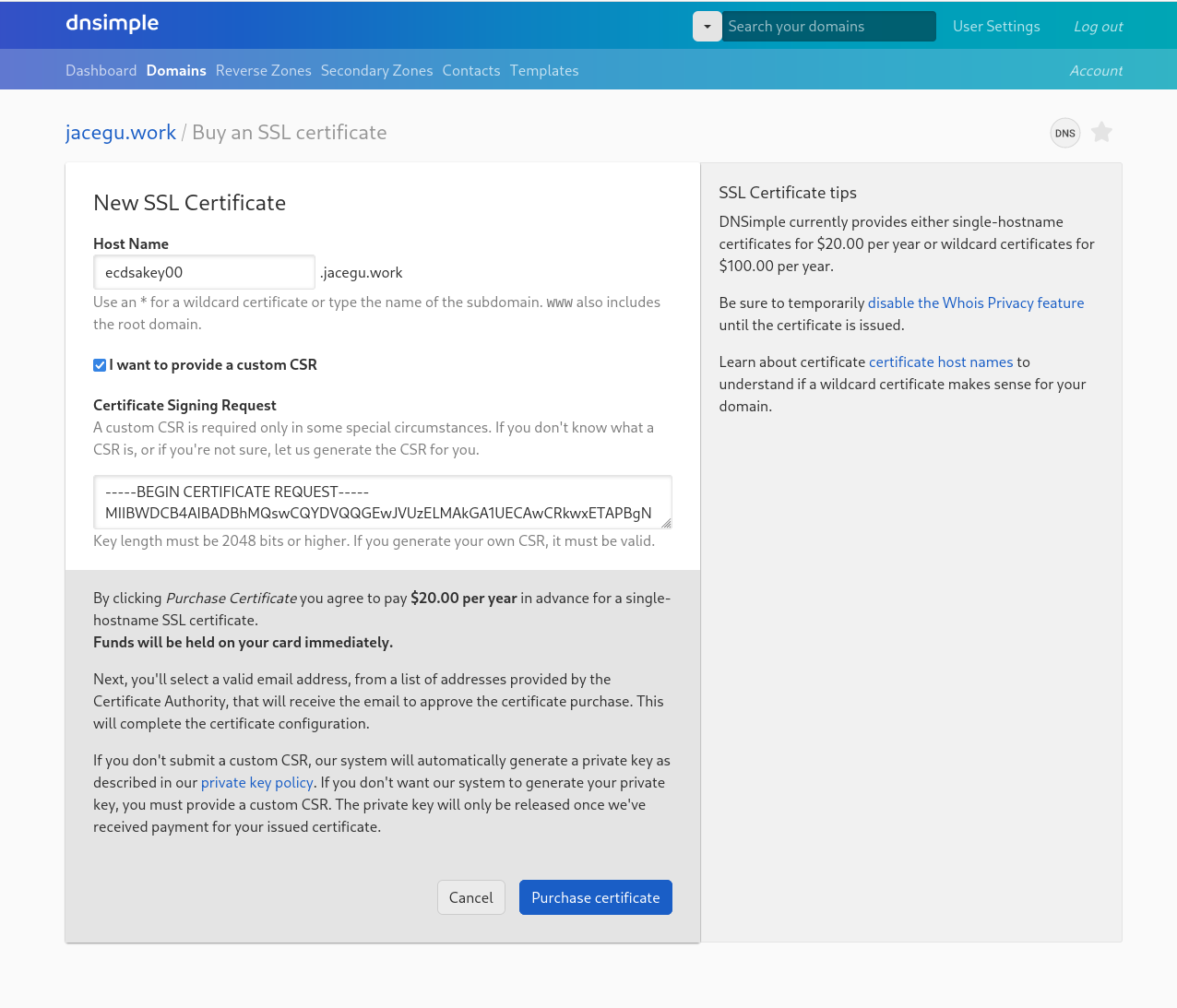
And upload the CSR we generated as part of our certificate ordering process:
And that's it. The same user experience you're familiar with applies here: you'll receive an email with the link and certificate code along with instructions to download and deploy in your web server.
How did we get here?
We work to help you keep your sites and APIs secure and reliable through DNS management and SSL Certificates purchased via Let's Encrypt and Sectigo. That means there's no reason to cut corners on security — just use DNSimple's certificate API or app to streamline the certificate-buying process.
ECC support for certificates is a step forward in enhancing security requirements — it requires less computational power, lower data transfer fees, and improves performance with smaller key size. Cryptography is continuously evolving; early algorithms and solutions are becoming obsolete with the technology we have right now. So if you have strong security requirements, ECC is a great choice.
Have questions or want to learn more? Drop us a line – we're always happy to help.
Not using DNSimple yet? Give us a try free for 30 days to experience our best-in-class domain and certificate management for yourself.
Néstor Salceda
Software engineer and open source lover.
We think domain management should be easy.
That's why we continue building DNSimple.

