DNSimple, Terraform & Sentinel — A Guide to Policy as Code
DNSimple is all about simple, reliable, secure domain management. We're a cloud-based DNS provider with an API that brings you easy integration with other tools and a wide range of features — like domain registration, management, and transfers, DNS record management, SSL certificates, and domain monitoring. We even support domain registration through Infrastructure as Code (IaC) tools like Terraform, which few other providers (if any) offer.
Our Terraform provider lets you manage domains and DNS records through Terraform, which in turn lets you use Sentinel, a Policy as Code (PaC) framework provided by HashiCorp, to enforce policies and rules on your infrastructure resources. Sentinel policies are written in a domain-specific language (DSL) that you can integrate into Terraform workflows to ensure compliance and security.
By integrating Sentinel policies with DNSimple's Terraform provider, organizations can enforce their domain management rules and guidelines, ensuring secure and compliant domain management. Let's talk more about IaC and PaC and how you can integrate them into your DNS management.
Infrastructure as Code and Policy as Code
Infrastructure as Code is a modern approach to managing and provisioning IT infrastructure. It provides a systematic, version-controlled, and automated way to define, deploy, and maintain infrastructure components. Policy as Code is an extension of IaC, which focuses on enforcing policies, rules, and guidelines on infrastructure resources.
Benefits of Policy as Code
Consistency — Enforcing policies through code ensures consistency across all infrastructure resources. Scalability — PaC scales effortlessly, enabling organizations to manage policies across various teams and projects. Reusability - Policy definitions can be shared and reused across different environments. Automation - Policy checks can be integrated into continuous integration and deployment (CI/CD) pipelines, enabling automated enforcement and reporting.
Implementing Policy as Code for domain management
Step 1: Set up your environment.
Configure your workspace and the DNSimple provider:
terraform {
cloud {
organization = "ACME"
workspaces {
name = "staging"
}
}
required_providers {
dnsimple = {
source = "dnsimple/dnsimple"
}
}
}
provider "dnsimple" {
token = var.dnsimple_token
account = var.dnsimple_account
sandbox = true
}
variable "dnsimple_token" {
type = string
sensitive = true
}
variable "dnsimple_account" {
type = string
}
Initialize Terraform and the DNSimple provider:
$ terraform init
Step 2: Define the domains and any other resources you want to manage using Terraform:
resource "dnsimple_contact" "alice_main" {
label = "Alice Appleseed"
first_name = "Alice main"
last_name = "Appleseed"
organization_name = "Acme"
job_title = "Managing Director"
address1 = "Level 1, 2 Main St"
address2 = "Marsfield"
city = "San Francisco"
state_province = "California"
postal_code = "90210"
country = "US"
phone = "+13215554333"
email = "alice@acme.com"
}
resource "dnsimple_registered_domain" "pineapple_pizza" {
name = "pineapple.pizza"
contact_id = 1234
auto_renew_enabled = false
whois_privacy_enabled = true
dnssec_enabled = true
}
Step 3: Create a Sentinel policy that defines your domain management rules:
import "tfplan/v2" as tfplan
import "tfconfig"
import "tfstate"
allRegisteredDomains = filter tfplan.resource_changes as _, resource_changes {
resource_changes.mode is "managed" and
resource_changes.type is "dnsimple_registered_domain" and
(resource_changes.change.actions contains "create" or
resource_changes.change.actions is ["update"])
}
default_contact_id = rule {
all allRegisteredDomains as _, domains {
domains.change.after.contact_id == tfstate.resources.dnsimple_contact.alice_main[0].attr.id
}
}
default_renewal_enabled = rule {
all allRegisteredDomains as _, domains {
domains.change.after.auto_renew_enabled == true
}
}
main = rule { default_contact_id or default_renewal_enabled }
Step 4: Configure your Terraform workspace to use Sentinel policies you created in the previous step by adding the policy to a policy set and associating it with your workspace. You can refer to the Terraform documentation for more information on how to do this.
Step 5: Apply Your Policies.
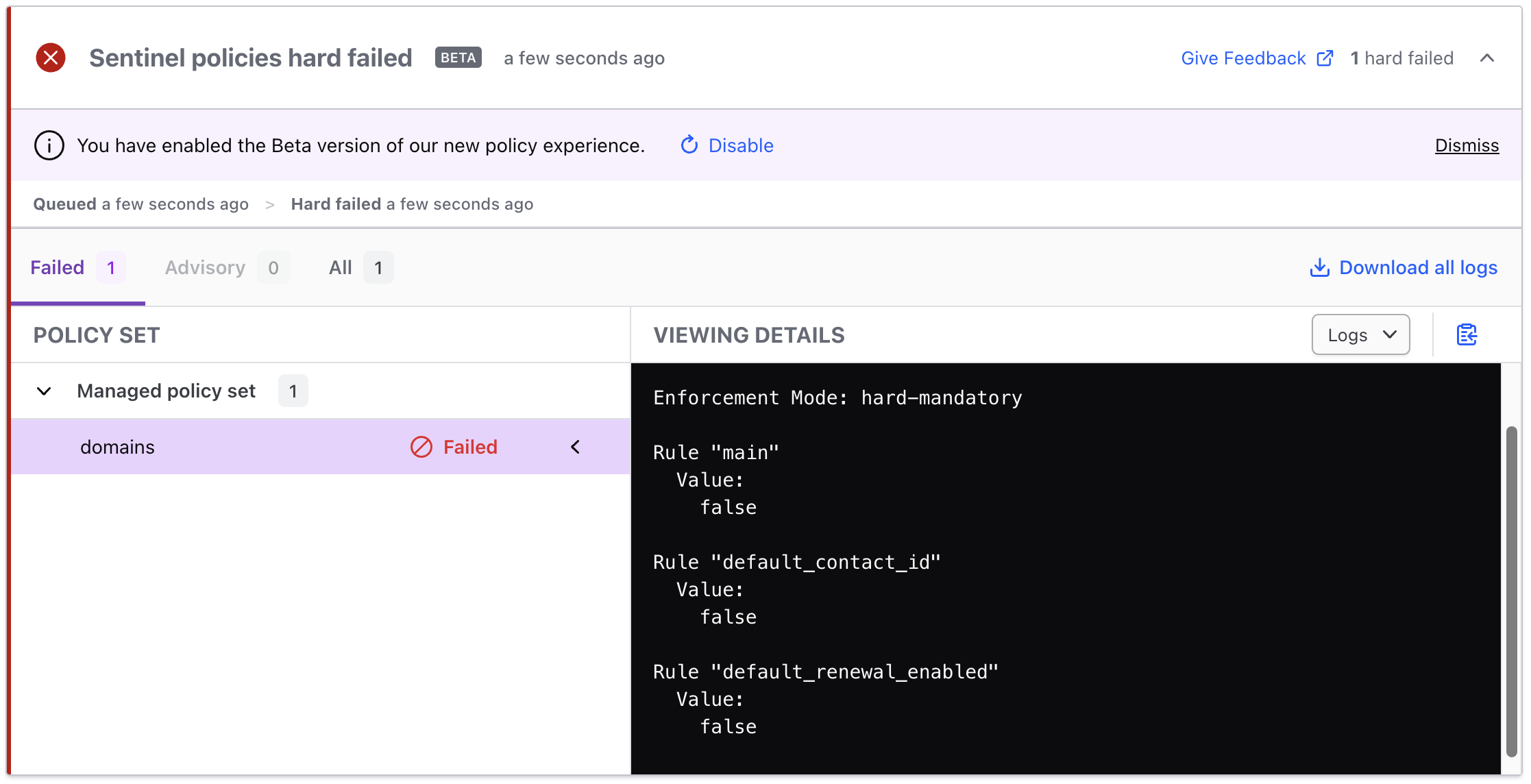
Run Terraform apply and see the policies and expect to see the Sentinel policies you created to be enforced preventing the apply from succeeding, unless the policies are met:
$ terraform apply
You can expect to see the following output in your Terraform Cloud console
Secure, compliant domain management
By leveraging the unique capabilities of DNSimple for domain registration via Infrastructure as Code, and combining it with the power of Sentinel for policy enforcement, organizations can automate their entire domain lifecycle to ensure secure, consistent, compliant domain management. Watch this video for more about using DNSimple with Terraform, or read our support documentation.
If you have more questions, or want to talk about how DNSimple can help you achieve the easiest domain management possible, drop us a line — we'd love to help.
Not using DNSimple yet? Give us a try free for 30 days to explore our integrations and multiple features that ensure your domain management is as simple and secure as possible.
Ivan Bakalov
Nothing is impossible, it's just a function of effort over time.
We think domain management should be easy.
That's why we continue building DNSimple.

